
Expert guidance to identify, assess, and reduce cyber risk through business-aligned advisory services.
CyberSecure Risk Management is a cybersecurity consulting firm specializing in strategic risk advisory services. We do not sell software, implement tools, or provide managed security services. Instead, we serve as your trusted advisor to help leadership make informed decisions about cybersecurity investments, risk prioritization, and security program maturity.
Our approach is rooted in Privacy by Design and business alignment. We work alongside your team to build resilient, sustainable security programs that support business objectives while reducing exposure to cyber threats.
Our flagship service: an ongoing strategic engagement to reduce cyber risk and improve security maturity.
Our Cyber Risk Management Consulting service is not a one-time assessment. It is a strategic, ongoing engagement designed to continuously identify, assess, and mitigate cybersecurity risks in alignment with your business priorities. We serve as an extension of your leadership team, providing the expertise and guidance needed to make informed security decisions.
This service is ideal for organizations that need executive-level cybersecurity guidance but may not have a full-time CISO or mature security program. We work with you to build a risk-aware culture, prioritize investments, and measure progress over time.
Quarterly Risk Assessments: Regular evaluation of your threat landscape, vulnerabilities, and control effectiveness.
Executive Risk Reporting: Clear, business-focused reports for leadership and boards that quantify risk and recommend prioritized actions.
Compliance Alignment: Guidance on meeting regulatory requirements such as HIPAA, PCI DSS, GDPR, CMMC, NIST, and SOC 2.
Security Program Development: We help you build policies, procedures, and controls that are practical and sustainable for your organization.
Incident Response Planning: Preparation for security incidents through documented playbooks, communication protocols, and tabletop exercises.
Continuous Improvement: Ongoing advisory support as threats evolve and your business changes.
We do not deliver one-time reports. We build a measurable, evolving risk reduction program tied to business outcomes.
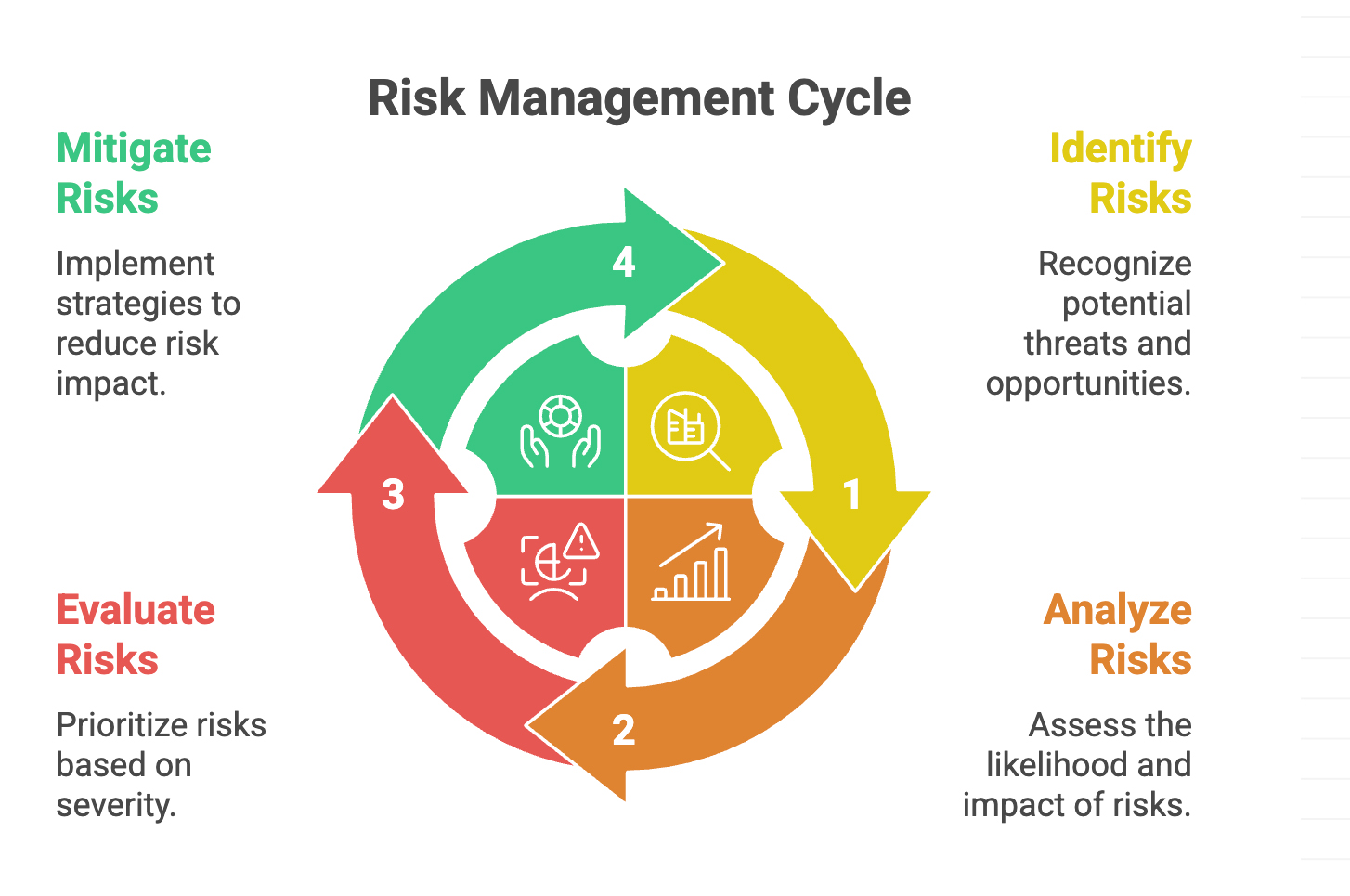
Every engagement follows our iterative Risk Management Cycle. This is not a linear checklist. It is a continuous process that ensures your organization stays protected as threats evolve and your business grows. We revisit this cycle quarterly to maintain security maturity and adapt to new risks.
This framework is critical because cyber threats are not static. New vulnerabilities emerge daily, attack methods become more sophisticated, and your business environment changes over time. By continuously cycling through these four phases, we help you maintain a robust security posture that aligns cybersecurity investments with business priorities.
How we operationalize the Risk Management Cycle in real client engagements.
Map assets, business processes, and potential attack vectors.
We begin by understanding your organization. We map critical business processes, digital assets, regulatory obligations, and third-party dependencies. This phase establishes a clear baseline of what needs protection and where vulnerabilities may exist, from network infrastructure to employee practices to vendor integrations.
Quantify risk by likelihood and business impact.
We evaluate identified risks using NIST-aligned assessment criteria. Each risk is scored based on likelihood and potential business impact, considering factors such as financial loss, operational disruption, regulatory penalties, and reputational damage. This creates a quantifiable risk profile that leadership can use to make informed decisions.
Prioritize risks based on criticality and risk tolerance.
Not all risks require immediate action. We work with your leadership to determine which risks exceed your tolerance and require mitigation, which can be accepted, and which can be monitored over time. This evaluation considers your business objectives, compliance requirements, and available resources to create a practical, prioritized action plan.
Execute corrective actions that reduce exposure and improve resilience.
We implement targeted controls and strategies to reduce high-priority risks to acceptable levels. These may include policy updates, technical controls, employee training, or process improvements. Our recommendations are practical, cost-effective, and designed to fit your organization. Then the cycle repeats quarterly to ensure continuous improvement.
Business-Aligned: Risk decisions are tied to business impact, not just technical severity, ensuring security investments support organizational goals.
Measurable Progress: Quarterly iterations allow you to track improvement over time and demonstrate security maturity to stakeholders.
Continuous Adaptation: The cyclical nature ensures risks are regularly reassessed as your business and threat landscape evolve.
Framework Compliance: Our methodology aligns with NIST, ISO 27001, and other industry frameworks, simplifying audit and compliance efforts.
Specialized engagements that complement our core consulting practice.
In addition to our flagship Cyber Risk Management Consulting service, we offer specialized advisory engagements that address specific security needs. These services can be delivered as standalone projects or integrated into an ongoing consulting relationship. Each is designed to strengthen your defenses, ensure compliance, and provide actionable guidance.

Independent evaluation of your organization's security controls, policies, and procedures. Our audits identify gaps in your security posture and provide actionable recommendations for improvement aligned with industry standards.

Focused analysis of specific systems, applications, or business processes to identify vulnerabilities, evaluate threats, and quantify risks. We provide detailed reports with prioritized recommendations based on business impact.

Systematic examination of your systems, networks, and applications to discover security weaknesses before attackers can exploit them. We use industry-leading tools and methodologies to identify technical vulnerabilities.

Evaluation of how privacy is integrated into your products, services, and business processes. We ensure privacy is embedded from the ground up, not added as an afterthought, helping you build trust with customers and meet regulatory expectations.

Strategic guidance on data privacy regulations, policies, and best practices. We help you navigate complex privacy laws and build a culture of privacy within your organization to protect customer data and avoid regulatory penalties.

Strategic recommendations for implementing advanced encryption technologies and data protection strategies to safeguard your sensitive information from unauthorized access, theft, or loss.
The advantages of partnering with strategic cybersecurity advisors.
We provide executive-level guidance aligned with business objectives, not just technical recommendations. Our advice helps leadership make informed decisions about security investments.
Identify and address vulnerabilities before they can be exploited, reducing your exposure to costly breaches and operational disruption.
We provide clear risk metrics that enable leadership to prioritize security spending based on business impact, not just technical severity.
Navigate complex regulatory requirements with confidence. We help you meet standards like HIPAA, PCI DSS, GDPR, CMMC, NIST, and SOC 2.
Unlike one-time assessments, our quarterly engagement model ensures your security program evolves as threats and business needs change.
We do not sell products or services from third parties. Our recommendations are unbiased and focused solely on what is best for your organization.
Benefit from years of experience in cybersecurity, risk management, and data privacy across multiple industries and regulatory environments.
We translate technical security issues into business language that executives and boards can understand and act upon.
We work alongside your team as a strategic partner and advocate, not just a consultant. Your success is our success.
Balancing the Scales of Justice in our Digital World
Let us help you build a strategic, measurable cybersecurity program that reduces risk and supports business growth. Whether you need ongoing advisory services or a focused engagement, we are here to provide expert guidance.
Book a 30 minute conversation to assess your cyber risk exposure.